This Ransomware prevention & protection guide takes a look at Ransomware prevention and the steps you can take to block & prevent Ransomware, the new malware which making news all around for the wrong reasons.
Time and again we learn about threats, and new variants of malware such as Ransomware that pose a danger to computer users. The ransomware virus locks access to a file or your computer and demands that a ransom be paid to the creator for regaining access, usually allowed via either an anonymous pre-paid cash voucher or Bitcoin. One specific ransomware threat that has managed to attract attention in recent times, is Cryptolocker, apart from FBI ransomware, Crilock & Locker.
The specialty of the ransomware is that it may come on its own (often by email) or by way of a backdoor or downloader, brought along as an additional component. Your computer could get infected with ransomware, when you click on a malicious link in an email, an instant message, a social networking site or in a compromised website - or if you download and open a malicious email attachment. Moreover, like a notorious virus, it may go undetected by most antivirus programs. And even if your antivirus software is able to remove the ransomware, many a time, you will just be left with a bunch of locked files and data!
How to prevent Ransomware
While the situation is worrisome and the outcome is fatal in most cases if you fail to comply with the malware author's rules - since the encrypted files can be damaged beyond repair - you can take certain preventive measures to keep the problem at bay. You can prevent ransomware encryption! Let us see some of the Ransomware prevention steps you can take. These steps can help you block & prevent Ransomware.
Updated OS & security software
Goes without saying that you use a fully updated modern operating system like Windows 10/8/7, a good antivirus software or an Internet Security Suite and an updated secure browser, and an updated email client. Set your email client to block .exe files.
Malware authors find computer users, who are running outdated versions of OS, to be easy targets. They are known to possess some vulnerabilities which these notorious criminals can exploit to silently get onto your system. So patch or update your software. Use a reputable security suite. It is always advisable to run a program that combines both anti-malware software and a software firewall to help you identify threats or suspicious behavior as malware authors frequently send out new variants, to try to avoid detection. You might want to read this post on Ransomware tricks & Browser behaviors.
Read about Ransomware protection in Windows 10.
Back up your data
You can certainly minimize the damage caused in the case of your machine getting infected with Ransomware by taking regular backups. In fact, Microsoft has gone all out and said that backup is the best defense against Ransomware including Cryptolocker.
Never click on unknown links or download attachments from unknown sources
This is important. Email is a common vector used by Ransomware to get on your computer. So never ever click on any link which you may think looks suspicious. Even if you have a 1% doubt - don't! The same holds true for attachments too. You can surely download attachments you are expecting from friends, relatives & associates, but be very careful of the mail forwards which you may receive even from your friends. A small rule to remember in such scenarios: If in doubt - DONT! Take a look at the precautions to take when opening email attachments or before clicking on web links.
RansomSaver is a very useful add-in for Microsoft's Outlook that detects and blocks emails that have ransomware malware files attached to them.
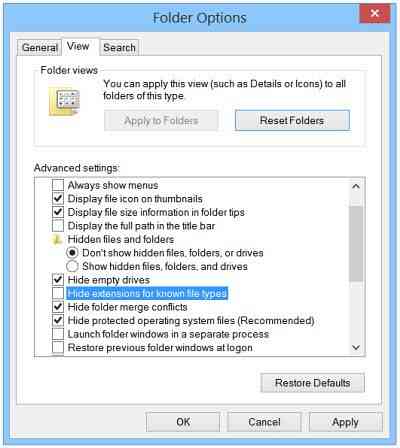
Show hidden file-extension

One file that serves as the entry route for Cryptolocker is the one named with the extension “.PDF.EXE”. Malware like to disguise their .exe files as harmless looking .pdf… doc or .txt files. If you enable the feature to see the full file extension, it can be easier to spot suspicious files and eliminate them in the first place. To show hidden file extensions, do the following:
Open Control Panel and search for Folder Options. Under the View tab, uncheck the option Hide extensions for known file types.
Click Apply > OK. Now when you check your files, the file names will always appear with their extensions like .doc, .pdf, .txt, etc. This will help you in seeing the real extensions of the files.
Disable files running from AppData/LocalAppData folders
Try to create and enforce rules within Windows, or use some Intrusion Prevention Software, to disallow a particular, notable behavior used by several Ransomware, including Cryptolocker, to run its executable from the App Data or Local App Data folders. The Cryptolocker Prevention Kit is a tool created by Third Tier that automates the process of making a Group Policy to disable files running from the App Data and Local App Data folders, as well as disabling executable files from running from the Temp directory of various unzipping utilities.
Application whitelisting
Application whitelisting is good practice that most IT administrators employ to prevent unauthorized executable files or programs from running on their system. When you do this, only software that you have whitelisted will be allowed to run on your system, as a result of which, unknown executive files, malware or ransomware will just not be able to run. See how to whitelist a program.
Disable SMB1
SMB or Server Message Block is a network file sharing protocol meant for sharing files, printers, etc, between computers. There are three versions - Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3). It is recommended that you disable SMB1 for security reasons.
Use AppLocker
Use Windows built-in feature AppLocker to prevent Users from installing or running Windows Store Apps and to control which software should run. You may configure your device accordingly to reduce the chances of Cryptolocker ransomware infection.
You can also use it to mitigate ransomware by blocking executable not signed, in places ransomware like:
\AppData\Local\Temp \AppData\Local\Temp\* \AppData\Local\Temp\*\*
This post will tell you how to create rules with AppLocker to an executable, and whitelist applications.
Using EMET
The Enhanced Mitigation Experience Toolkit protects Windows computers against cyber-attacks & unknown exploits. It detects and blocks exploitation techniques that are commonly used to exploit memory corruption vulnerabilities. It prevents exploits from dropping Trojan, but if you click open a file, it will not be able to help. UPDATE: This tool is not available now. Windows 10 Fall Creators Update will include EMET as a part of Windows Defender, so users of this OS need not use it.
Protect MBR
Protect your computer's Master Boot Record with MBR Filter.
Disable Remote Desktop Protocol
Most Ransomware, including the Cryptolocker malware, tries to gain access to target machines via Remote Desktop Protocol (RDP), a Windows utility that permits access to your desktop remotely. So, if you find RDP of no use to you, disable remote desktop to protect your machine from File Coder and other RDP exploits.
Disable Windows Scripting Host
Malware and ransomware families often make use of WSH to run .js or .jse files to infect your computer. If you have no use for this feature, you can disable Windows Scripting Host to stay safe.
Use Ransomware prevention or removal tools
Use a good free anti-ransomware software. BitDefender AntiRansomware and RansomFree are some of the good ones. You may use RanSim Ransomware Simulator to check if your computer is sufficiently protected.
Kaspersky WindowsUnlocker can be useful if the Ransomware totally blocks access to your computer or even restrict access to select important functions, as it can clean up a ransomware infected Registry.

If you can identify the ransomware, it can make things a bit easier as you can use the ransomware decryption tools that may be available for that particular ransomware.
Here is a list of free Ransomware Decryptor Tools that can help you unlock files.
Disconnect from the Internet immediately
If you are suspicious about a file, act quickly to stop its communication with the C&C server before it finishes encrypting your files. To do so, simply disconnect yourself from the Internet, WiFi or your Network immediately, because the encryption process takes time so although you cannot nullify the effect of Ransomware, you can certainly mitigate the damage.
Use System Restore to get back to a known-clean state
If you have System Restore enabled on your Windows machine, which I insist that you have, try taking your system back to a known clean state. This is not a fool-proof method, however, in certain cases, it might help.
Set the BIOS clock back
Most Ransomware, including Cryptolocker, or the FBI Ransomware, offer a deadline or a time limit within which you can make the payment. If extended, the price for the decryption key can go up significantly, and - you cannot even bargain. What you can at least try is “beat the clock” by setting the BIOS clock back to a time before the deadline hour window is up. The only resort, when all tricks fail as it can prevent you from paying the higher price. Most ransomware offer you a 3-8 days period and may demand even up to USD 300 or more for the key to unlocking your locked data files.
While most of the targeted groups by Ransomware have been in the US and the UK, there exists no geographical limit. Anyone can be affected by it - and with every passing day, more and more ransomware malware is being detected. So take some steps to prevent Ransomware from getting onto your computer. This post talks a little more about Ransomware Attacks & FAQ.
Now read: What to do after a Ransomware attack.

 Phenquestions
Phenquestions