md5() Function
md5() function uses Message-Digest algorithm for encryption. This function calculates the md5 hash value of the original value. The syntax of this function is given below.
Syntax:
string md5 (string $string, [ bool $raw])This function can take two arguments. The first argument is mandatory that is used to take the string value that will be encrypted. The second argument is optional that is used to store any Boolean value. The function returns a 32-bit hexadecimal number if the optional argument is not used, and returns a 16-bit hexadecimal number if the optional value is TRUE.
Example: Use of md5()
The following example shows the use of the md5() function to encrypt any data. Create a PHP file with the following script to see how this function works.
In the script, $original_string variable is used to store a string value that is encrypted later by using the md5() function. Both the original value and the encrypted values will be printed after executing the script.
//Define a string value$original_string = 'LinuxHint';
//Print the original value
echo "
The original data :
". $original_string;//Encrypt the string value
$encrypted_string = md5($original_string);
//Print the encrypted value
echo "
The encrypted data after using md5() :
$encrypted_string";?>
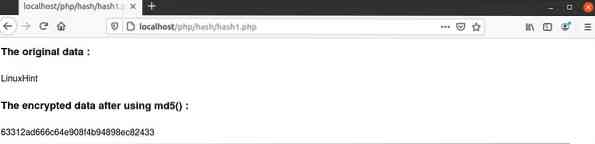
Output:
The following output will appear after running the script from the server. No optional argument is used in md5() function. So, the output shows 32-bit hexadecimal numbers as output.
sha1() Function
This function uses Secure Hash Algorithm 1 for encryption. The syntax of this function is given below.
Syntax:
string sha1 (string $string, [ bool $raw])This function can take two arguments like the md5() hashing algorithm. The first argument takes the string value that will be encrypted. The optional argument takes any Boolean value. If no optional argument is passed, then the function returns a 40-characters hexadecimal number. If the optional value is set to TRUE, then the function returns raw binary data.
Example: Use of sha1()
The following example shows the use of the sha1() function to encrypt any data. Create a PHP file with the following script to see how this function works.
In the script, $original_string variable is used to store a string value that is encrypted later by using the sha1() function with and without the optional argument. Both the original value and the encrypted values will be printed after executing the script.
//Define a string value$original_string = 'LinuxHint';
//Print the original value
echo "
The original data :
". $original_string;//Encrypt the string value
$encrypted_string = sha1($original_string);
//Print the encrypted value
echo "
The encrypted data after using sha1() :
$encrypted_string";//Encrypt the string value
$encrypted_string2 = sha1($original_string,TRUE);
//Print the encrypted value
echo "
The encrypted data after using sha1() with optional argument:
$encrypted_string2";?>
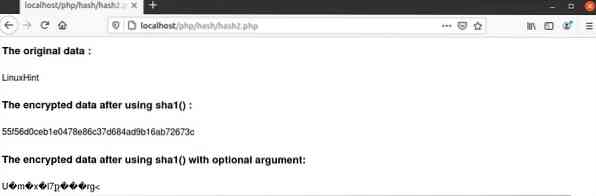
Output:
The following output will appear after running the script from the server. It shows a 40-characters hexadecimal number when no optional argument is used in the sha1() function and the output shows raw data when TRUE is used in the optional argument value of the sha1() function.
hash() Function
the hash() function is used to generate the hash value of the particular string based on any hashing algorithm. The syntax of this function is given below.
string or false hash (string $algorithm, string $data [, bool $binary = false])This function can take three arguments. The first argument takes the algorithm name that will be used to generate the hash value of the string value given in the second argument. The third argument is optional. This function returns lowercase hex digits if the optional value is false and returns raw binary data if the optional value is true. Many hashing algorithms exist in PHP to generate hash data by using the hash() function. hash_alogs() function can be used to find out the list of existing hash algorithms.
Example: Use of hash()
The following example shows the use of the hash() function to generate the hash value using any particular hashing algorithm. Create a PHP file with the following script to see how this function works.
'ripemd160' hashing algorithm is used in the hash() function to generate the hash value. The hash() function is used with and without the optional argument in the script. Both the original value and the encrypted values will be printed after executing the script.
//Define a string value$original_string = 'LinuxHint';
//Print the original value
echo "
The original data :
". $original_string;//Encrypt the string value
$encrypted_string = hash('ripemd160', $original_string);
//Print the encrypted value
echo "
The encrypted data after using hash() :
$encrypted_string";//Encrypt the string value
$encrypted_string2 = hash('ripemd160', $original_string, TRUE);
//Print the encrypted value
echo "
The encrypted data after using hash() with optional argument:
$encrypted_string2";?>
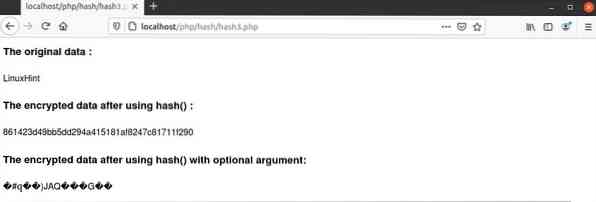
Output:
The following output will appear after running the script from the server. It shows the hexadecimal number as a hash value when no optional argument is used, and the raw data when the optional argument is used in the hash() function.
Conclusion
The important data is required encrypting for the making of any web application security. Different ways of encrypting data are shown in this tutorial by using multiple hash functions of PHP. The uses of three built-in hash functions are explained in this tutorial to generate the encrypted data using the PHP script.
 Phenquestions
Phenquestions


