For developing zero-day, there are two options either you develop your own or capture zero-day developed by others. Developing zero-day on your own can be a monotonous and long process. It requires great knowledge. It can take a lot of time. On the other hand, zero-day can be captured developed by others and can be reused. Many hackers use this approach. In this program, we set up a honeypot that appears as unsafe. Then we wait for the attackers to get attracted to it, and then their malware is captured when they broke into our system. A hacker can use the malware again in any other system, so the basic goal is to capture the malware first.
Dionaea:
Markus Koetter was the one who developed Dionaea. Dionaea is chiefly named after the plant carnivorous Venus flytrap. Primarily, it is a low interaction honeypot. Dionaea comprises of services that are attacked by the attackers, for instance, HTTP, SMB, etc., and imitates an unprotected window system. Dionaea uses Libemu for detecting shellcode and can make us vigilant about the shellcode and then capture it. It sends concurrent notifications of attack via XMPP and then records the information into an SQ Lite database.
Libemu:
Libemu is a library used for the detection of shellcode and x86 emulation. Libemu can draw malware inside the documents such as RTF, PDF, etc. we can use that for hostile behavior by using heuristics. This is an advanced form of a honeypot, and beginners should not try it. Dionaea is unsafe if it gets compromised by a hacker your whole system will get compromised and for this purpose, the lean install should be used, Debian and Ubuntu system are preferred.
I recommend not to use it on a system that will be used for other purposes as libraries and codes will get installed by us that may damage other parts of your system. Dionaea, on the other hand, is unsafe if it gets compromised your whole system will get compromised. For this purpose, the lean install should be used; Debian and Ubuntu systems are preferred.
Install dependencies:
Dionaea is a composite software, and many dependencies are required by it that are not installed on other systems like Ubuntu and Debian. So we will have to install dependencies before installing Dionaea, and it can be a dull task.
For example, we need to download the following packages to begin.
$ sudo apt-get install libudns-dev libglib2.0-dev libssl-dev libcurl4-openssl-devlibreadline-dev libsqlite3-dev python-dev libtool automake autoconf
build-essential subversion git-core flex bison pkg-config libnl-3-dev
libnl-genl-3-dev libnl-nf-3-dev libnl-route-3-dev sqlite3
A script by Andrew Michael Smith can be downloaded from Github using wget.
When this script is downloaded, it will install applications (SQlite) and dependencies, download and configure Dionaea then.
$ wget -q https://raw.github.com/andremichaelsmith/honeypot-setup-script/master/setup.bash -O /tmp/setup.bash && bash /tmp/setup.bash
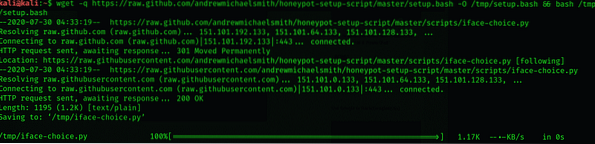
Choose an interface:
Dionaea will configure itself, and it will ask you to select the network interface you want the honeypot to listen on after the dependencies and applications are downloaded.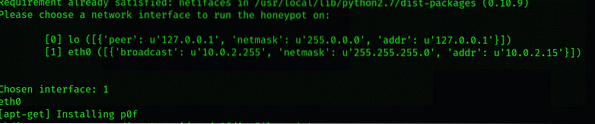
Configuring Dionaea:
Now honeypot is all set and running. In future tutorials, I will show you how to identify the items of the attackers, how to set up Dionaea in real times of attack to alert you,
And how to look over and capture the shellcode of the attack. We will test our attack tools and Metasploit to check if we can capture malware before placing it live online.
Open the Dionaea configuration file:
Open the Dionaea configuration file in this step.
$ cd /etc/dionaea
Vim or any text editor other than this can work. Leafpad is used in this case.
$ sudo leafpad dionaea.confConfigure logging:
In several cases, multiple gigabytes of a log file is seen. Log error priorities should be configured, and for this purpose, scroll down the logging section of a file.
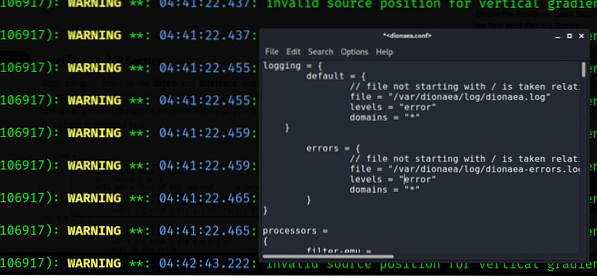
Interface and IP section:
In this step, scroll down to the interface and listen to a portion of the configuration file. We want to have the interface to be set to manual. As a result, Dionaea will capture an interface of your own choice.
Modules:
Now the next step is to set the modules for the efficient functioning of Dionaea. We will be using p0f for operating system fingerprinting. This will help to transfer data into the SQLite database.
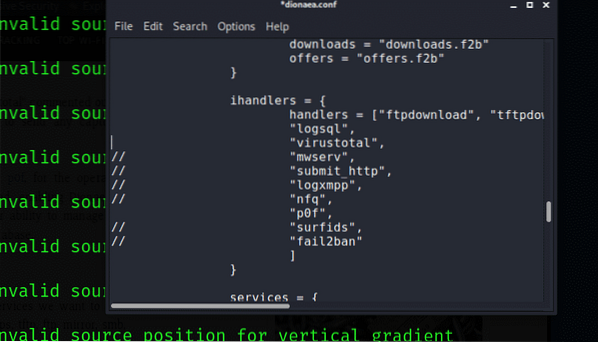
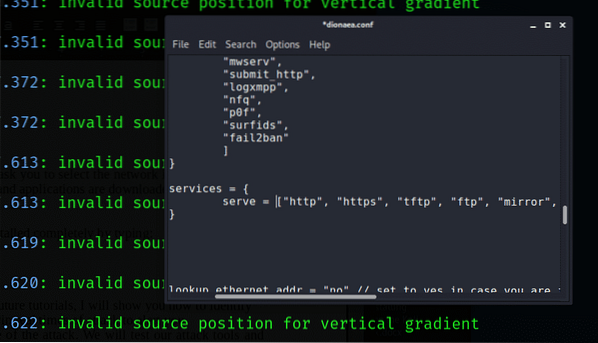
Services:
Dionaea is set up to run https, http, FTP, TFTP, smb, epmap, sip, mssql, and mysql
Disable Http and https because hackers are not likely to get fooled by them, and they are not vulnerable. Leave the others because they are unsafe services and can be attacked easily by hackers.
Start dionaea to test:
We have to run dionaea to find our new configuration. We can do this by typing:
$ sudo dionaea -u nobody -g nogroup -w /opt/dionaea -p /opt/dionaea/run/dionaea.pid 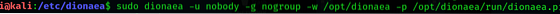
Now we can analyze and capture malware with the help of Dionaea as it is running successfully.
Conclusion:
By using the zero-day exploit, hacking can become easy. It is computer software vulnerability, and a great way to attract attackers, and anyone can be lured into it. You can easily exploit computer programs and data. I hope this article will help you learn more about Zero-Day Exploit.
 Phenquestions
Phenquestions


