But today, we'll talk about another great port scanner: Unicornscan, and how to use it in your next attempt at portscanning. Like other popular tools for portscanning such as nmap, it has several great features that are unique to itself. One such feature is that it can send out packets and receive them through two different threads, unlike other portscanners.
Known for its asynchronous TCP and UDP scanning capabilities, Unicornscan enables its users to discover details on network systems through alternative scanning protocols.
Unicornscan's attributes
Before we attempt a network and port scan with unicornscan, let's highlight some of its defining features:
- Asynchronous stateless TCP scanning with each of the TCP flags or flag combinations
- Asynchronous protocol-specific UDP scanning
- superior interface for measuring a response from a TCP/IP enabled stimulus
- Active and Passive remote OS and application detection
- PCAP file logging and filtering
- capable of sending packets with different OS fingerprints than the OS of the host.
- Relational database output for storing the results of your scans
- Customizable module support to fit according to the system being pentested
- Customized data set views.
- Has its TCP/IP stack, a distinguishing feature that sets it apart from other port scanners
- Comes built into Kali Linux, no need to download
Performing a simple scan with Unicornscan
The most basic scan withUnicornscan allows us to scan a single host IP. Type the following in the interface to perform the basic scan with Unicornscan
$ sudo unicornscan 192.168.100.35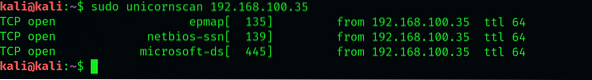
Here, we've tried this scan on a system with Win 7 connected to our network. The basic scan has listed all the TCP ports on the system we're scanning. Notice the similarities to -sS scan in nmap, and how the key is that it doesn't use ICMP by default. Out of the ports mentioned, only ports 135,139,445 and 554 are open.
Scanning multiple IPs wit Unicornscan
We will make a slight modification in the basic scan syntax to scan multiple hosts, and you'll notice the subtle difference from scan commands we use in nmap and hping. The targets are placed in sequence to initiate scanning:
$ sudo unicornscan 192.168.100.35 192.168.100.45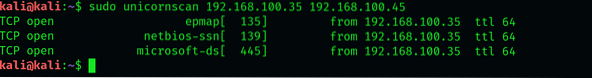
Make sure you're not placing any commas between the addresses, else the interface will not recognize the command.
Scanning Class C networks with Unicornscan
Let's move on to scan our entire class C network. We will use a CIDR notation such as 192.168.1.0/24 to scan all 255 host IP addresses. If we were to find all the IPs with port 31 open, we'd add: 31 after the CIDC notation:
$ sudo unicornscan 192.168.100.35/24:31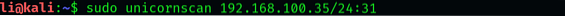
Unicornscan has successfully returned us to all the hosts that have port 31 open. The cool thing about unicornscan is that it doesn't stop at our network, where speed is a limiting factor. Suppose that all systems with ports 1020 open had a certain vulnerability. Without even having any idea about where these systems are, we can scan all of them. Although scanning such a large number of systems can take ages, it would be better if we divide them into smaller scans.
TCP scanning with Unicornscan
Unicornscan is well able to perform TCP scans as well. We'll designate websiteX.com as our target and scan for ports 67 and 420. For this specific scan, we'll be sending 33 packets per second. Before mentioning the ports, we'll instruct unicornscan to send 33 packets per second by adding -r33 in the syntax and -mT to indicate we want to scan (m) using the TCP protocol. The website name shall proceed with these flags.
$ sudo unicornscan -r33 -mT linuxhint.com:67,420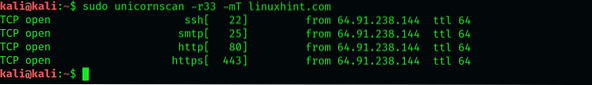
UDP scanning:
We can also scan for UDP ports with unicornscan. Type:
$ sudo unicornscan -r300 -mU linuxhint.com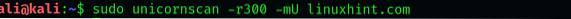
Notice that we've replaced the T with a U in the syntax. This is to specify that we're looking for UDP ports since Unicornscan only sends TCP SYN packets by default.
Our scan has not reported any open UDP ports. This is because open UDP ports are typically a rare find. However, it is possible that you may come across an open 53 port or a 161 port.
Saving results to a PCAP file
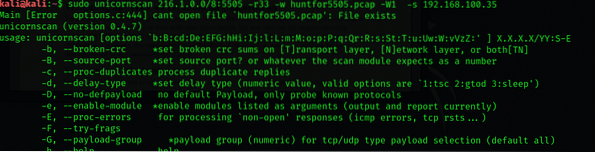
You can export the received packets to a PCAP file at a directory of your choice and perform network analysis later. To find hosts with port 5505 open, type
$ sudo unicornscan 216.1.0.0/8:5505 -r500 -w huntfor5505.pcap-W1 -s 192.168.100.35
Wrapping up -Why we recommend Unicornscan
Simply put, it does everything that a typical port scanner does and does it better. For example, scanning is much quicker with unicornscan than with other portscanners, because they use the target's operating system's TCP/IP stack. This comes in particularly handy when you're scanning massive corporate networks as a pentester. You may come across hundreds of thousands of addresses, and time becomes a deciding factor of how successful the scan is.
Unicornscan Cheat Sheet
Here's a quick cheat sheet to help with basic scans with Unicornscan that might come in handy.
SYN : -mTACK scan : -mTsA
Fin scan : -mTsF
Null scan : -mTs
Xmas scan : -mTsFPU
Connect Scan : -msf -Iv
Full Xmas scan : -mTFSRPAU
scan ports 1 through 5 : (-mT) host:1-5
Conclusion:
In this tutorial, I have explained the unicornscan tool and how to use it with an example. I hope you learn the basics, and this article helps you in pentesting via Kali Linux.
 Phenquestions
Phenquestions